Breaking: Ludhiana Police busted International Call Center
In a major breakthrough Ludhiana Police have busted an International Call Center operating illegally and arrested an entire gang of 30 persons who posed as Technical Service Providers for Multinational Companies and duped global citizens, mainly foreigners for huge amount of money.

Ludhiana, July 21, 2023: In a major breakthrough Ludhiana Police have busted an International Call Center operating illegally and arrested an entire gang of 30 persons who posed as Technical Service Providers for Multinational Companies and duped global citizens, mainly foreigners for huge amount of money.
The arrested accused have been identified as: Sachin, Bal Krishna, Cleareeb Khyreim, Deepak Shah, Yadav Sandeep, Kuldip, Kevika, Kupattu, Krishan Singh, Aman Singh, Amar Singh, Yadav Santosh, Mishra Chirag, Suraj Rai, Vikas Singh, Hardik Bharatbai Solanki, Parveen Sehgal, Vini Dev, Harman Singh, Suraj Thakur, Gagangdeep Singh, Kausili, Mohaka Aumi, Lovpreet Singh, Rahul Thakur, Arjun Singh Sahota, Vikas Yadav and Kamlesh pal.
Of the accused 2 are from Ludhiana, 1 each from Gurdaspur, Delhi and Himachal Pradesh, 3 each from UP and Nagaland, 7 from Gujarat, 11 from Meghalaya.
The recovereies made from the accused are as under: electronic tab (14), mobile phone (34), laptop (2), Cash Rs.1,17,000, activa (1), emptry boxes of tab (15) abd documents.
Meanwhile, Commissioner of Police, Ludhiana Mandeep Singh Sidhu has released Ludhiana Call Centre's Modus Operandi, which is as under:
1. INSERTION POINTS- TARGETTING VICTIMS
There are several ways, or “insertion points,” where victims are targeted in the fraud scheme. In this case, the insertion point is a pop-up on the victim’s computer caused by the victim mistyping a URL in his/her browser where the pop-up claims the victim’s computer has been hacked and providing a technical support number to call.
2. FRAUDULENT SCRIPTS
These scripts are often a pre-written script that the conspirators used to initiate the fraud. In this case, the conspirators pretend to be a computer technical support company, which either offers to address an existing issue in the victim’s computer.
They follow a step by step process whereby first they try to convince the victim that his computer has been hacked. This is done using a remote control software
3. REMOTE CONTROL SOFTWARE
Once the telephone call is initiated, the scammer (known as THE DIALER) instructs the victim to download commercially available remote desktop software, such as UltraViewer, and to allow the conspirator to connect to the victim’s computer to address or diagnose whatever issue initiated the contact.
The victim contacts the call center because the victim’s computer has allegedly been “compromised,” then the conspirator will pretend to diagnose the problem by connecting to the computer to diagnose the issue.
After remote desktop software is downloaded and installed by the victim, the conspirator then connects to the victim’s computer from a remote location. The remote desktop software allows the conspirator to have virtually full control of the computer as though the individual is sitting in from of the victim’s computer.
While on the phone and connected to the victim’s computer, the conspirator often pretends to run diagnostic software on the computer. But rather than running diagnostic software, the conspirators often use command-line programs that are built into Microsoft
Windows, such as the Microsoft Command Prompt (shown below), to trick the victim into thinking that the conspirator is actually doing something productive.
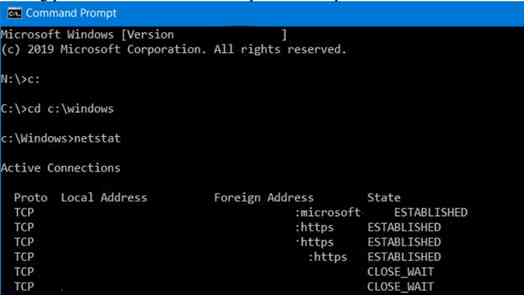
The victim’s computer is alleged compromised, the conspirator uses these basic Windows tools to claim allegedly rogue connections to the computer.
The DIALER also convinces the victim that there are subscriptions that the victim has applied for
4. WITHDRAWAL AND REFUND SCAM
On having convinced the victim that his laptop is compromised, the DIALER says that only the Federal Trade Commission can deal with his issue since it involves financial transactions.
The DIALER then allegedly transfers the call to THE CLOSER who pretends to be a representative of the Federal Trade Commission. The CLOSER convinces the victim that he will help the victim secure his computer.
In order to secure the computer, the CLOSER convinces the victim to withdraw money from his bank account. they ask the customer to drive to their respective bank branch and withdraw the money in amounts of $500. They warn the customer not to tell the bank branch anything about the call as they feel the branch officials may be involved in having the victim’s computer and stealing their money. So this is their way of securing the money of the victims. They say they will monitor the victim’s bank accounts for them and will try and trace the hackers.
After the customer withdraws the amount, they ask the customer to cover this cash into some traceable electronic mode such as gift card or bit coins and make the customer tell them the card number. They then tell the customer that they’ll put the money back into their accounts and secure them.
The bitcoins/gift cards are redeemed by another person (named Alex) and sent through Hawala to the manager (Cheri and Yadav brothers) of this and other call centers.


 City Air News
City Air News 










